Securing Your Vue App with JWT and Express: Modern Authentication for Full-Stack Developers
In today's rapidly evolving software landscape, robust authentication is non-negotiable. With the proliferation of single-page applications (SPAs) and the rise of decoupled architectures, securing your Vue.js applications with JSON Web Tokens (JWT) and Express.js is now a standard best practice. This comprehensive guide will walk you through modern authentication trends in 2024, provide production-grade code examples, and offer actionable security insights for full-stack developers.
JWT (JSON Web Token) has become the de facto standard for stateless authentication in modern web applications, thanks to its scalability, flexibility, and security properties. According to a 2024 survey by Stack Overflow, over 68% of full-stack developers use JWT for authentication in their Node.js-based APIs. Express.js remains the most popular backend framework in the Node ecosystem, and pairing it with Vue.js on the frontend forms a robust stack for secure, scalable applications.
This article provides a step-by-step guide to implementing JWT authentication in a Vue.js app with an Express backend, including setup, configuration, secure token handling, advanced patterns, error handling, and real-world deployment tips. By following the best practices and code samples herein, you'll be equipped to build secure, production-ready full-stack applications.

// Example: Express.js JWT Authentication Middleware
const jwt = require('jsonwebtoken');
function authenticateToken(req, res, next) {
const authHeader = req.headers['authorization'];
const token = authHeader && authHeader.split(' ')[1];
if (!token) return res.status(401).json({ message: 'Token required' });
jwt.verify(token, process.env.JWT_SECRET, (err, user) => {
if (err) return res.status(403).json({ message: 'Invalid token' });
req.user = user;
next();
});
}
module.exports = authenticateToken;1. Understanding JWT Authentication in Full-Stack Development
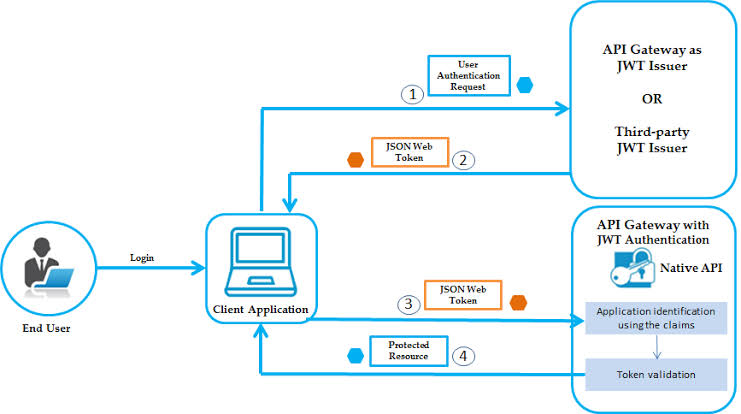
JWT, or JSON Web Token, is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. In full-stack development, JWT enables stateless authentication, reducing server load and simplifying scaling.
The token is usually composed of three parts: Header, Payload, and Signature. When a user logs in, the server generates a JWT and sends it to the client, which stores it (usually in memory or a secure cookie). On subsequent requests, the client includes this token in the `Authorization` header, allowing the server to validate the user's identity.
- **Header:** Algorithm & token type
- **Payload:** Claims (user info, permissions)
- **Signature:** Verifies the token wasn't altered
// Example: Creating a JWT
const jwt = require('jsonwebtoken');
const user = { id: 42, username: 'alice' };
const token = jwt.sign(user, process.env.JWT_SECRET, { expiresIn: '1h' });
console.log('JWT:', token);// Example: Decoding a JWT (on the backend)
try {
const decoded = jwt.verify(token, process.env.JWT_SECRET);
console.log('Decoded payload:', decoded);
} catch (err) {
console.error('JWT error:', err);
}{
"header": { "alg": "HS256", "typ": "JWT" },
"payload": { "id": 42, "username": "alice", "iat": 1712196576, "exp": 1712200176 },
"signature": "..."
}"JWT enables stateless authentication, boosting performance and scalability for modern full-stack apps.""
2. Setting Up Your Express Backend for JWT Authentication
Let's start by scaffolding our Express.js backend, integrating JWT authentication, and preparing for secure token issuance and validation. We'll use `jsonwebtoken` for JWT operations and `dotenv` for config management. Keeping dependencies updated is critical, as security vulnerabilities are patched frequently in the Node ecosystem.

# 1. Initialize a new Node.js project
npm init -y
# 2. Install dependencies
npm install express jsonwebtoken dotenv cors bcryptjs mongoose# .env
PORT=4000
JWT_SECRET=supersecret_jwt_key// server.js: Basic Express Setup
require('dotenv').config();
const express = require('express');
const cors = require('cors');
const app = express();
app.use(cors());
app.use(express.json());
app.listen(process.env.PORT, () => {
console.log(`Server running on port ${process.env.PORT}`);
});// routes/auth.js
const express = require('express');
const jwt = require('jsonwebtoken');
const bcrypt = require('bcryptjs');
const router = express.Router();
// Dummy user
db
const users = [{ id: 1, username: 'alice', password: '$2a$10$...' }];
router.post('/login', async (req, res) => {
const { username, password } = req.body;
const user = users.find(u => u.username === username);
if (!user) return res.status(401).json({ message: 'Invalid credentials' });
const valid = await bcrypt.compare(password, user.password);
if (!valid) return res.status(401).json({ message: 'Invalid credentials' });
const token = jwt.sign({ id: user.id, username: user.username }, process.env.JWT_SECRET, { expiresIn: '1h' });
res.json({ token });
});
module.exports = router;// Integrate auth routes in server.js
const authRoutes = require('./routes/auth');
app.use('/api/auth', authRoutes);3. Implementing JWT Authentication in Your Vue.js Frontend
On the frontend, Vue.js provides a flexible, reactive environment for handling authentication flows. We'll build a login form, handle token storage, and use Axios for secure API communication. It's critical to store tokens securely; in most cases, store the JWT in memory (Vuex or Pinia) or a secure, httpOnly cookie to mitigate XSS vulnerabilities.

# Create new Vue app
npm install -g @vue/cli
vue create vue-jwt-auth-app
cd vue-jwt-auth-app
npm install axios vuex// store/index.js (Vuex)
import Vue from 'vue';
import Vuex from 'vuex';
import axios from 'axios';
Vue.use(Vuex);
export default new Vuex.Store({
state: { token: '', user: null },
mutations: {
setToken(state, token) { state.token = token; },
setUser(state, user) { state.user = user; }
},
actions: {
async login({ commit }, credentials) {
const { data } = await axios.post('http://localhost:4000/api/auth/login', credentials);
commit('setToken', data.token);
// Optionally decode and store user info
commit('setUser', JSON.parse(atob(data.token.split('.')[1])));
},
logout({ commit }) {
commit('setToken', '');
commit('setUser', null);
}
},
getters: {
isAuthenticated: state => !!state.token
}
});// Login.vue (component)
<template>
<form @submit.prevent="onLogin">
<input v-model="username" placeholder="Username" />
<input v-model="password" type="password" placeholder="Password" />
<button type="submit">Login</button>
</form>
</template>
<script>
import { mapActions } from 'vuex';
export default {
data() { return { username: '', password: '' }; },
methods: {
...mapActions(['login']),
async onLogin() {
try {
await this.login({ username: this.username, password: this.password });
this.$router.push('/dashboard');
} catch (e) {
alert('Login failed');
}
}
}
}
</script>// axios.js (Axios instance with JWT auth)
import axios from 'axios';
import store from './store';
const instance = axios.create({ baseURL: 'http://localhost:4000/api' });
instance.interceptors.request.use(config => {
const token = store.state.token;
if (token) config.headers.Authorization = `Bearer ${token}`;
return config;
}, error => Promise.reject(error));
export default instance;// Before/After: Adding JWT to Axios
// BEFORE
axios.get('/api/protected');
// AFTER
import axios from './axios';
axios.get('/protected');4. Protecting Express Endpoints and Advanced Authorization
After integrating JWT issuance and storage, the next step is to protect sensitive endpoints and implement advanced authorization logic. This involves creating middleware to verify JWTs and optionally check user roles or permissions. A common approach is to attach the `authenticateToken` middleware to protected routes and define role-based access controls (RBAC).

// middleware/auth.js
function authorizeRoles(...roles) {
return (req, res, next) => {
if (!req.user || !roles.includes(req.user.role)) {
return res.status(403).json({ message: 'Forbidden: insufficient role' });
}
next();
};
}
module.exports = { authorizeRoles };// routes/admin.js
const express = require('express');
const { authorizeRoles } = require('../middleware/auth');
const authenticateToken = require('../middleware/authenticateToken');
const router = express.Router();
router.get('/dashboard', authenticateToken, authorizeRoles('admin'), (req, res) => {
res.json({ message: 'Welcome, admin!' });
});
module.exports = router;// server.js (add admin routes)
const adminRoutes = require('./routes/admin');
app.use('/api/admin', adminRoutes);// Error handling middleware
app.use((err, req, res, next) => {
console.error('Server error:', err);
res.status(500).json({ message: 'Internal server error' });
});// Vue: Handling 403 errors in frontend
axios.get('/admin/dashboard').catch(err => {
if (err.response && err.response.status === 403) {
alert('Access denied: insufficient permissions');
}
});5. Security Best Practices for JWT in Vue and Express
Security is never set-and-forget. The following best practices are essential for robust JWT authentication in 2024:
- Always use strong, unpredictable secrets in production (`JWT_SECRET`)
- Set short token expiration times; use refresh tokens if needed
- Store JWT in httpOnly cookies for maximum XSS protection, or in memory if not possible
- Never store JWT in localStorage if XSS is a risk
- Rotate secrets and use key identifiers (`kid`) for multi-key setups
- Validate JWT signature and claims (issuer, audience, expiration)
- Keep dependencies updated and monitor for vulnerabilities
According to the 2024 Snyk State of JavaScript Security Report, 44% of Node.js vulnerabilities stem from outdated packages. Automate dependency updates and use tools like `npm audit` regularly.

// Secure JWT cookie example (Express)
res.cookie('token', token, {
httpOnly: true,
secure: process.env.NODE_ENV === 'production',
sameSite: 'strict',
maxAge: 3600000 // 1 hour
});// JWT signature validation
token = req.cookies.token;
jwt.verify(token, process.env.JWT_SECRET, (err, decoded) => {
if (err) return res.status(403).send('Invalid token');
req.user = decoded;
next();
});# Dependency and vulnerability scanning
npm outdated
npm audit
npm audit fix// Refresh token endpoint (simplified)
router.post('/refresh', (req, res) => {
const refreshToken = req.body.token;
if (!refreshToken) return res.sendStatus(401);
// Verify and issue new JWT...
});// Vue: Securely log out (clear JWT)
store.dispatch('logout');
document.cookie = 'token=; Max-Age=0; path=/;';6. Testing, Error Handling, and Debugging JWT Authentication
Robust authentication requires comprehensive testing and graceful error handling. Test authentication flows using tools like Postman, Jest, and Cypress. On the backend, always handle JWT errors explicitly, and on the frontend, provide clear UI feedback for authentication errors.

// Express: JWT error middleware
function jwtErrorHandler(err, req, res, next) {
if (err.name === 'UnauthorizedError') {
return res.status(401).json({ message: 'Invalid token' });
}
next(err);
}
app.use(jwtErrorHandler);// Jest: Testing protected endpoint
const request = require('supertest');
const app = require('../server');
describe('GET /api/admin/dashboard', () => {
it('should reject unauthorized access', async () => {
const res = await request(app).get('/api/admin/dashboard');
expect(res.statusCode).toBe(401);
});
});// Vue: Show error message on authentication failure
<template>
<div v-if="error">{{ error }}</div>
<!-- ... -->
</template>
<script>
export default {
data() { return { error: '' }; },
methods: {
async onLogin() {
try {
// ...
} catch (e) {
this.error = 'Invalid username or password';
}
}
}
}
</script># Cypress: E2E test for login
npx cypress open{
"scripts": {
"test": "jest",
"e2e": "cypress run"
}
}7. Performance Optimization and Scaling JWT Authentication
Performance is key for large-scale applications. JWT authentication, being stateless, naturally scales well. However, consider the following for optimal performance:
- Keep JWT payloads lean (avoid sensitive or large data)
- Use Redis or in-memory stores for blacklisting tokens (logout, revocation)
- Enable gzip or Brotli compression for API responses
- Use CDN or edge caching for static content
- Monitor API response times and error rates

// Express: Enable gzip compression
const compression = require('compression');
app.use(compression());// Example token blacklist using Redis
const redis = require('redis');
const client = redis.createClient();
function blacklistToken(token) {
client.set(token, 'blacklisted', 'EX', 3600); // expires in 1 hour
}
function isBlacklisted(token, callback) {
client.get(token, (err, result) => {
callback(result === 'blacklisted');
});
}// API response time monitoring
const responseTime = require('response-time');
app.use(responseTime());// Vue: Minimize JWT payload usage
const user = this.$store.state.user;
// Only use non-sensitive fields for UI rendering8. Real-World Deployment: Production Ready JWT & Express + Vue
Deploying a full-stack Vue.js and Express app with JWT authentication involves several additional considerations for production readiness:
- Enforce HTTPS for all API and client communication
- Set CORS policies strictly (allow only trusted origins)
- Use environment variables for all secrets
- Enable helmet middleware for security headers
- Regularly audit and update dependencies
- Monitor server logs for unusual activity

// Express: Enforce HTTPS
app.use((req, res, next) => {
if (process.env.NODE_ENV === 'production' && !req.secure) {
return res.redirect('https://' + req.headers.host + req.url);
}
next();
});// CORS setup for trusted frontend
const corsOptions = {
origin: ['https://yourfrontend.com'],
credentials: true
};
app.use(cors(corsOptions));// Helmet for security headers
const helmet = require('helmet');
app.use(helmet());// Logging middleware
const morgan = require('morgan');
app.use(morgan('combined'));// Vue: Axios base URL for production
axios.defaults.baseURL = 'https://api.yourdomain.com';Conclusion: Building Secure, Scalable Vue + Express Apps in 2024
JWT authentication, when implemented with care, equips your full-stack Vue.js and Express applications for the challenges of modern web security. By following the patterns, best practices, and actionable code examples in this guide, you can deliver robust, scalable authentication to your users and project stakeholders.
Key takeaways:
- Use JWT for scalable, stateless authentication
- Pair Express.js and Vue.js for flexible full-stack apps
- Store tokens securely and follow best practices
- Test, monitor, and update regularly
- Automate security and performance checks as you scale

Ready to harden your authentication? Start by implementing the sample code, audit your stack, and keep learning. Secure coding is a journey, not a destination.
Thanks for reading!